Web3 usage by threat actors
The innovations in the blockchain and web3 space have introduced new threat vectors that state-sponsored and financially-motivated actors alike could utilize in their operations.
Background and use cases
Abuse of legitimate web services is as old as the internet itself. Content Delivery Networks (“CDNs”) and other public cloud services are often abused in a myriad of ways, from hosting malware, command & control servers and even to create deepfakes in support of information warfare operations and the creation of certain narratives.
Due to the decentralized nature of Web3 infrastructure, it is only natural that threat actors would eventually abuse Web3 services and incorporate it into their typical attack chain. Here are some of the observed malicious use cases observed:
The InterPlanetary File System

IPFS for short, a peer-to-peer storage network. In summary, much like the BitTorrent protocol, a file provided to the IPFS network is distributed across different objects then when the object is requested, the protocol would reassemble the file and serve it to the user, as a web page, for example. It appears that at this time, most of the cases involving IPFS abuse are phishing and hosting malware payloads. It’s also worth noting that - again - due to the decentralized nature of the protocol, it is extremely difficult to takedown content hosted on the network.
Cryptojacking
Cryptojacking refers to the act of illegally using other people’s device resources to mine cryptocurrency, it can come in many forms from malware to more advanced procedures such as what TeamTNT has been doing with vulnerable, publicly-facing cloud workloads.
Cryptojacking is often mapped on MITRE ATT&CK as T1496 - Resource Hijacking. It’s very unlikely for a (financially-motivated) threat actor to mine a substantial amount using a dozen of infect devices, as such, they may turn to mining pools. Participants “pool” their collective resources for mining efforts and split earnings.
It’s worth noting that not all mining pools follow KYC procedures which makes it even more attractive to cybercrime actors.
As a Command & Control (C2) channel and layer of obfuscation
Although a bit novel and academic, it is possible to use blockchain infrastructure as a command & control channel. Blockchains often have a “testnet”, a network available for developers to test blockchain implementations for no cost of actual cryptocurrency thus giving an avenue for threat actors to use it as a command & control channel.
In the real life however, a more practical utilization of the blockchain can be seen with the Glupteba malware, Sophos made an exellent report that showcases how the malware can retrieve C2 server addresses from just querying Bitcoin transaction IDs.
CTI / OSINT opportunities and considerations
Public IPFS gateways are listed for everyone and can be used as a baseline to make a blocklist to go from. Enterprise proxies often categorize the gateways as “file sharing” which in a typical enterprise environment it is blocked. Nevertheless, the list can be found below too, I have personally seen at least 3 of the gateways listed in phishing campaigns:
ipfs.io
dweb.link
ipfs.io
dweb.link
gateway.ipfs.io
ninetailed.ninja
via0.com
ipfs.eternum.io
hardbin.com
cloudflare-ipfs.com
astyanax.io
cf-ipfs.com
ipns.co
gateway.originprotocol.com
gateway.pinata.cloud
ipfs.sloppyta.co
ipfs.busy.org
ipfs.greyh.at
gateway.serph.network
jorropo.net
ipfs.fooock.com
cdn.cwinfo.net
aragon.ventures
permaweb.io
ipfs.best-practice.se
storjipfs-gateway.com
ipfs.runfission.com
ipfs.trusti.id
ipfs.overpi.com
ipfs.ink
ipfsgateway.makersplace.com
ipfs.funnychain.co
ipfs.telos.miami
ipfs.mttk.net
ipfs.fleek.co
ipfs.jbb.one
ipfs.yt
hashnews.k1ic.com
ipfs.drink.cafe
ipfs.kavin.rocks
ipfs.denarius.io
crustwebsites.net
ipfs0.sjc.cloudsigma.com
ipfs.genenetwork.org
ipfs.eth.aragon.network
ipfs.smartholdem.io
ipfs.xoqq.ch
natoboram.mynetgear.com
video.oneloveipfs.com
ipfs.anonymize.com
ipfs.scalaproject.io
search.ipfsgate.com
ipfs.decoo.io
alexdav.id
ipfs.uploads.nu
hub.textile.io
ipfs1.pixura.io
ravencoinipfs-gateway.com
konubinix.eu
ipfs.tubby.cloud
ipfs.lain.la
ipfs.kaleido.art
ipfs.slang.cx
ipfs.arching-kaos.com
storry.tv
ipfs.1-2.dev
dweb.eu.org
permaweb.eu.org
ipfs.namebase.io
ipfs.tribecap.co
ipfs.kinematiks.com
c4rex.co
nftstorage.link
gravity.jup.io
tth-ipfs.com
ipfs.chisdealhd.co.uk
ipfs.alloyxuast.tk
ipfs.litnet.work
4everland.io
ipfs-gateway.cloud
w3s.link
cthd.icu
ipfs.joaoleitao.org
ipfs.tayfundogdas.me
As it currently stands, the only good search engine that I could find for the IPFS protocol seems to be ipfs-search.com, It has decent filtering capability and seems to support search syntaxes.
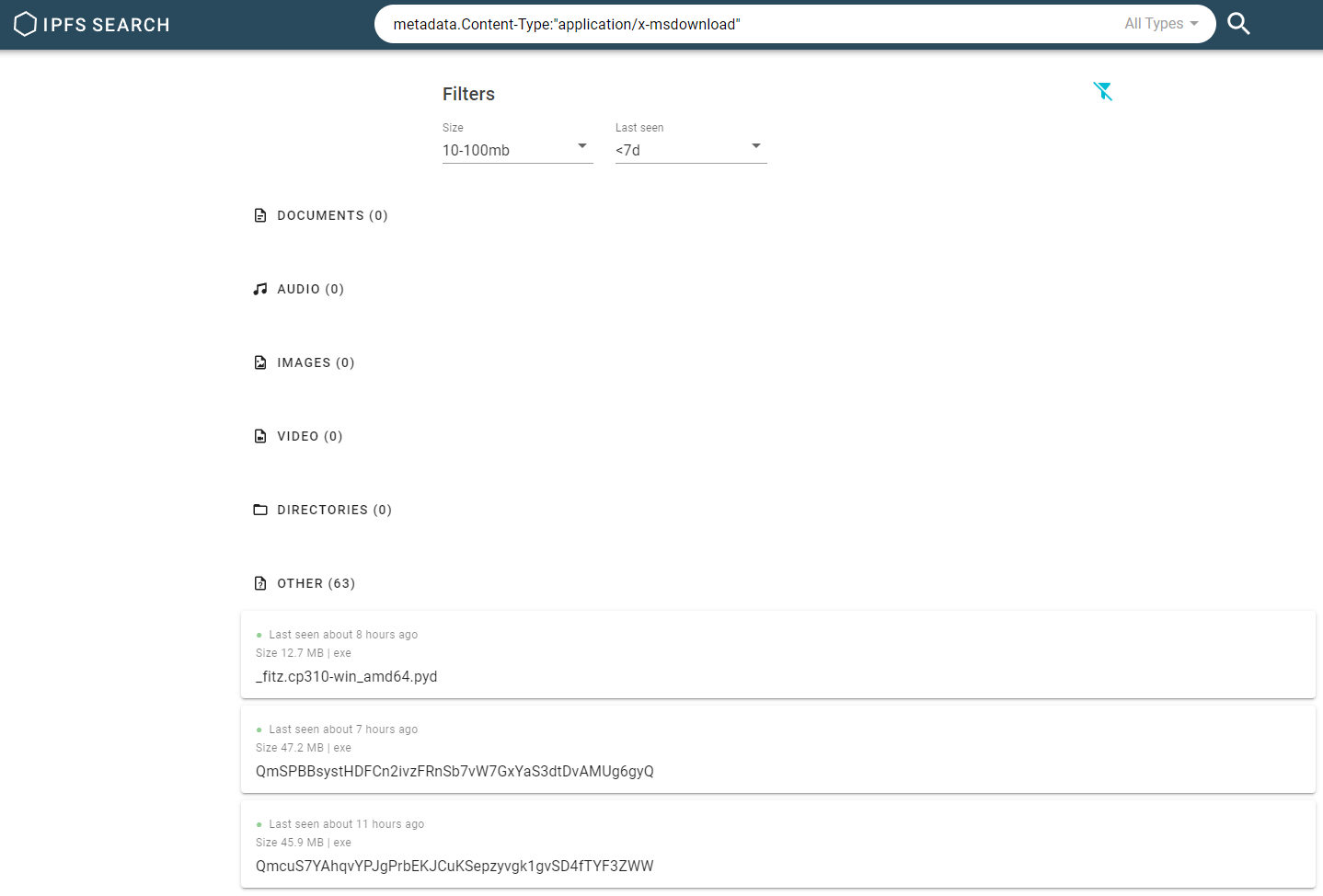 Here I found some executables already, seems like a good (threat) hunting ground to me! Furthermore, it seems that it would be a great collection source for those interested in aggregating such binaries.
Here I found some executables already, seems like a good (threat) hunting ground to me! Furthermore, it seems that it would be a great collection source for those interested in aggregating such binaries.
As for cryptojacking, it would be a good threat hunting opportunity to look for hosts that make connections to mining pools. Even though they are usually blocked by common enterprise proxy solutions, it’s worth aggregating a list and monitoring for hits.
References and further reading
- SecurityAffairs: Threat actors abuse Microsoft Azure to Host Malware and C2 Servers
- Bleeping Computer: Google quietly bans deepfake training projects on Colab
- Cisco Talos: Threat Spotlight: Cyber Criminal Adoption of IPFS for Phishing, Malware Campaigns
- Mandiant: The IO Offensive: Information Operations Surrounding the Russian Invasion of Ukraine
- COINTELEGRAPH: IPFS rep explains how malicious files are eliminated from its network
- Ars Technica: The bitcoin blockchain is helping keep a botnet from being taken down
- Akamai: Bitcoins, Blockchains, and Botnets
- Github: ilmoi/mining-pools-aggregator